Those damn hackers hacked my Facebook!
“Don’t watch the video I inboxed you, my FB has been Hacked by Hackers!”
Seen this before? Seen this more than once? You probably have. Accounts on Facebook have been hacked and taken over by hackers and they are working hard to hack your friends and families accounts… Or have they? Are they really? Who are these Hackers? And whilst we are on this subject, what are Hackers?
Read further to understand what is usually actually going on, who is doing all these account takeovers and what the difference is between a Hacker and a criminal actor/criminal.
Foreword
Facebook, Instagram, Twitter, TikTok, MySpace, Gmail and all the rest. These social media sites have been around for quite some time and will be around for many more. Account takeovers are here to stay, and will probably get worse before they get better and lesser. During this article we will attempt to help you understand what happened to your account, how and why that happened, and give some useful tips and advice to protect yourself and your connections in the future.
Be the Social Media Hero you were born to be, read this blog and be the “All Informed” friend you were born to be.
What is a Hacker and should I be afraid?
So this person that broke into your account using computer wizardry and devilish intent is a hacker correct? Not quite…
Taken from Wikipedia
“A computer hacker is a computer expert who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means.
Though the term “hacker” has become associated in popular culture with a “security hacker” – someone who utilizes their technical know-how of bugs or exploits to break into computer systems and access data which would otherwise be unavailable to them – hacking can also be utilized by legitimate figures in legal situations. For example, law enforcement agencies sometimes use hacking techniques in order to collect evidence on criminals and other malicious actors. This could include using anonymity tools (such as a VPN, or the dark web) to mask their identities online, posing as criminals themselves.[1][2] Likewise, covert world agencies can employ hacking techniques in the legal conduct of their work.”
The term Hacker is a derivative of the phase/ethos known as “Hacking Culture”. This culture began back in the 1960s at MIT, where students banded together to release information on the internet they thought should be public information. Often referred to as, “computer-science freaks”.
So with the above in mind, you can now see that Hackers are not the bad guys, in fact most Hackers believe in privacy, freedom of information, freedom of speech, they help to secure the very same internet you are using to browse this article and furthermore help secure the technology on your computer or smartphone. They are either working for the companies that build the technology you use in your everyday life, or they are independent, unvested security researchers telling/disclosing found vulnerabilities to the hackers in the tech companies.
Hackers Good. Cyber Criminals, bad.
Basics on personal security on social media
On almost all social media sites on the internet efforts have been made to keep your information and data private and secured. They have also taken steps to help identify who you are (A username typically, or an email address) and to validate or verify your identity they have put passwords in place. Passwords are there to validate that the username being used to log into an account by you or someone else is, infact you.
Password management on a website tends to be determined by the website creators, and ideally this is governed by a security standard or known and approved methodology. Some websites however enforce more rules than others.
- Some websites may only require a 8 character password
- Some websites may require a 8 character password with Capital letters and Numbers
- Some websites may require 8+ character length with Capital letters, Numbers and special characters.
- Some websites may only allow you to use a 8 character length password, and thankfully some will let you use a password longer than 64 characters.
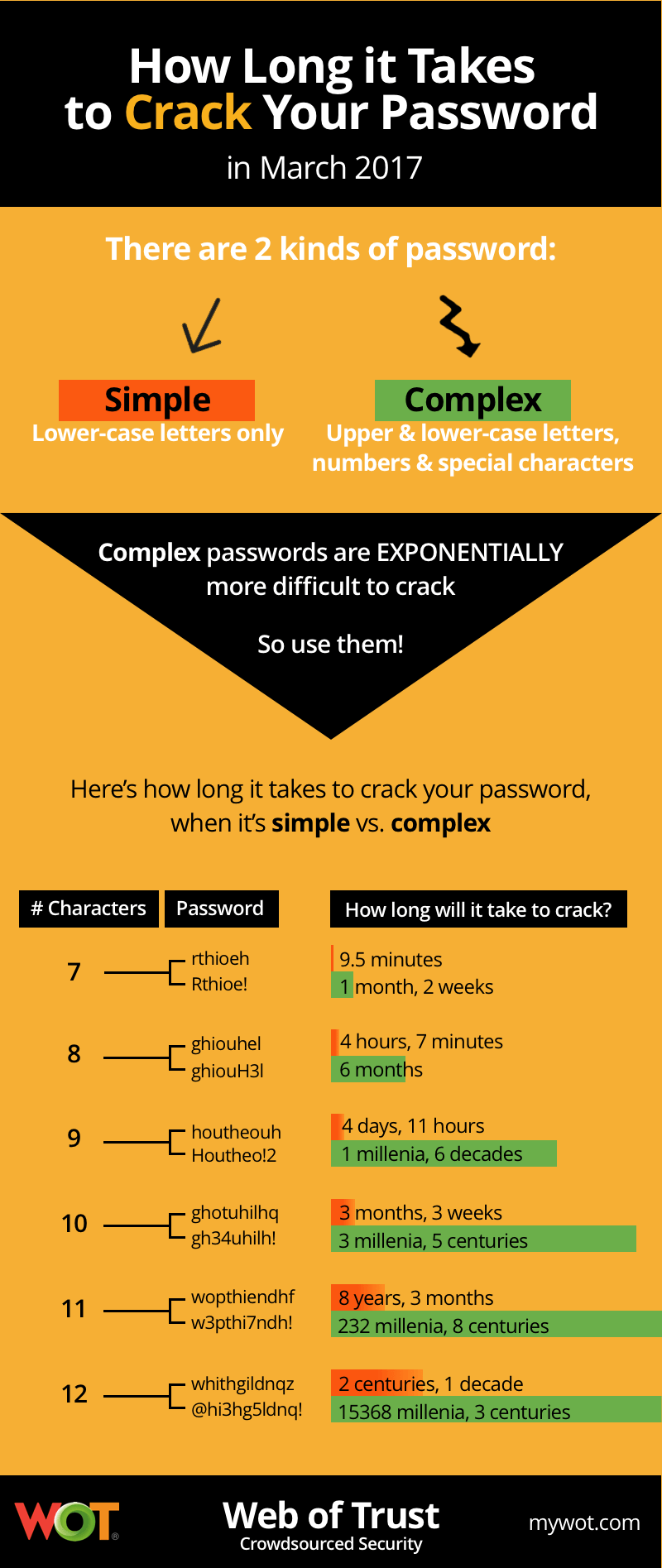
As a direct example, Facebook enforces that the password must be at least six characters and should be a mix of uppercase and lowercase characters, numbers and punctuation.
We will illustrate the importance of “Longer and complex is best practice”
Why me? Why this account?
Your account was breached for many reasons, most likely not targeted, unless you have a huge following, a following that can be financially valuable.
The biggest reason is most likely the simple fact that your email and password are publicly available due to it being in a breach/leak of some sort.
Account cloning has been known to target pensioners as they are sadly easy targets and probably don’t have the the technical access to see something is wrong or perhaps even know something is wrong.
When it comes to accounts with a high following, it is more likely to be targeted. The attacker can take over the account, wipe your content and see the account with all its followers to someone else. Another common occurrence is that “Influencers” will share their account details with promoters/marketing people or SEO boosters, instead of using a service that can keep your account safe. If your promoter gets compromised, so do you. Try using a service where multiple users can access the same account, with different login details with varying privileges.
We will look for better options that would allow you to do that and try to give some insights. In the meantime we have already found the following:
How was my account taken over?
Typically the attack path is as follows. Once upon a time you created a profile somewhere and maybe do not recall. That website that was linked to a company maybe didn’t secure your information correctly (ie. storing passwords in clear text) or they left their database/servers insecure, often by mistake or not following standard guidelines.
Somewhere in the world, a motivated individual found this vulnerability on the site’s application and probably tried to tell the company they have a known vulnerability. Sometimes companies do not pay attention to this or snub it off. This motivated individual perhaps loses their patience and thinks “What better way is there for this company to take its users privacy seriously” and downloads their database and posts online for the world to see. This tends to get the users attention.
Now with a breach like this, if they released the database they found there will be an assortment of personal data.
This can include:
- Your Name
- Your address
- Your email address
- Your password (That you used for this website)
- Other PII (Personal Identifying Information)
Now if you used unique, complex passwords (Long complex passwords that are only used once, and different passwords for each site) then the effect on you will be limited to that website and the information released. But, if you are maybe unaware or somewhat lazy, you might be using the same password in multiple places, or (not as bad but still bad) you use variations of the same password. Eg. (Spring=2020FB, Spring=2020IG)
With the former, a motivated individual can use your email to scan for website where you are registered, like Facebook, Twitter, Instagram, Netflix, etc. They can then manually - or by using automation - scan for these sites that have your email address, trying the password that they have and the automated way will return a notification to them that they managed to log in. Now usually, this would not be the end of the road for you. There is something you can do to limit the risk above and still stay secure, which is 2FA/MFA (2 Factor Authentication/Multi Factor Authentication). Yes, the assailant could log into your account but they still would not have access, because they would have to prove once again that they are you. If they dont have your authentication application set up, they aren’t getting in.
For now though, lets consider you don’t have 2FA set up, and they are in. They can then check if you are an admin on a Facebook page. They can kick all other admins, make one of there alternative accounts admin and then they own the page. The play here is that they could do some of the following bad things.
If your page has a decent amount of followers they can rebrand it and sell it (with the followers you acquired) They can use your page to post Phishing links They can use your page to unsuspectedly change donation banking details so that if someone wants to make a donation to NPO “Help the kids” they actually end up paying “Joe Soap scammer Ltd.”
Has my personal data been in a breach?
So, there is a Security Researcher called Troy Hunt and he built a website called haveibeenpwned and what this site does is it hunts for all these breaches. They get access to the leaked databases, they verify it and then load that database to their own database. The thing is, Troy actually works extremely hard to secure his stuff and encrypts everything.
Below is what they have in their database. This also includes the recent Experian Breach.
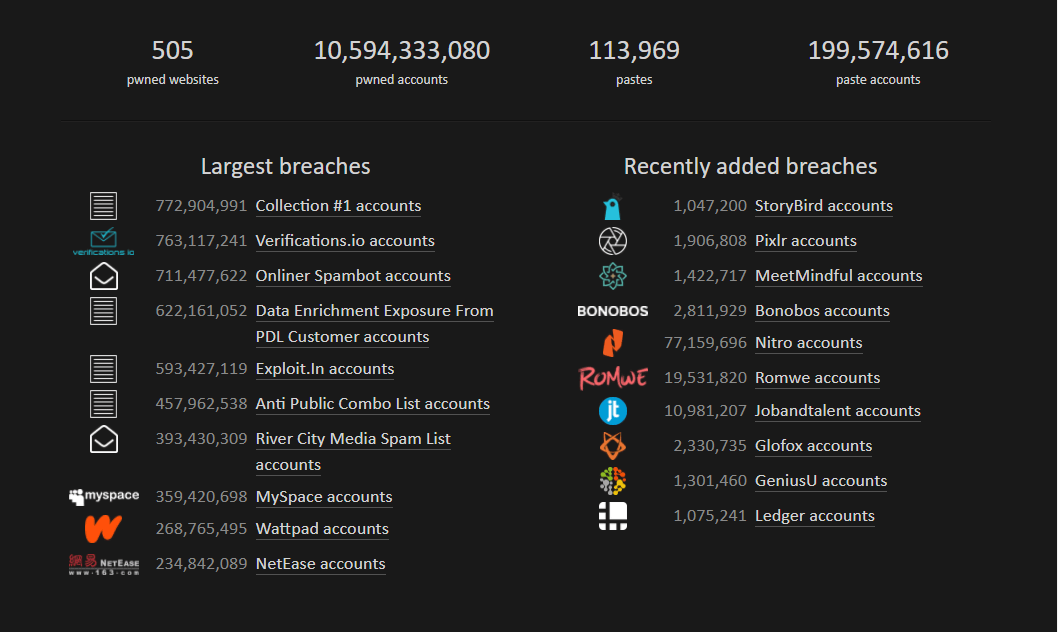
All you do is take your email address and search it in the search bar. It will then compare this to the haveibeenpwned database and if there is a record (or multiple) it will return and show you in what breaches you were a victim. See below:

So you might be asking yourself, “Hey Hack South, my Facebook was hacked, what does this have to do with my email address?” It’s simple. There are 2 core reasons.
Firstly, if you used the same password on your email, you might have used that password on your Social Media account. This is bad, but not the worst.
Secondly, and far worse is that by having access to your email, they could gain access to everything you have, linked to that email. They dont need to know your social media accounts! All they do is take your email address, go to their desired account and do a password reset. If you dont have 2FA the reset link will come to your email, which they have access to and then they just change your password. Its that easy. The other implication is that with this they could poke around your email, hijack online deliveries, check out your Google photos account and find NSFW pictures which they could blackmail you with.
Having access to your email address is like them having your front door key to your entire online presence. Once again, 2FA solves this problem.
As you can see with this section, these aren’t some elite level, government sponsored, NCIS Cyber hacking abilities. It0s as simple as them going to a “Digital Library” and taking they publicly accessible “Breach Yellow Pages” book labelled “The 2 Billion user accounts breached and leaked” and looking you up on the internet. Nothing like this….
What should I do first after my account takeover?
There is a saying among hackers. “Burn it, burn it with fire”. For you and I it means the following: “Burn it with fire” means if you have had 1 account breached, consider them all breached, especially if you use the same password for multiple accounts.
If your Facebook has been compromised, go into your email account and change the password. If you use a Password manager, use a new, 64 Character password and enable 2FA (Using your phone number or Google Authenticator or Authy. Once you have changed your email passwords try to log into your Facebook or start an account recovery. If your account has been properly taken over, the assailant will have changed your username, your password and enabled 2FA.
If the above happens things get really tricky. You first want to try to regain access to your email through a complaint logging system, which we will not be covering here. If you still have access, reset your password and enable 2FA.
How do I gain access again?
On most social media sites you can report your own profile as being compromised. It also helps to ask your friends to go on your profile and report it as compromised.
Facebook has a how to guide which you can review here. Once reports pile up Facebook will deactivate the account and investigate. They will then contact you to do the reset. MAKE SURE it is from a legitimate FB email account. Hopefully they can recover anything that was lost or changed, but you have to prepare yourself for the worst.
My Account/Friends account has been cloned? Why and how?
This is more simple to explain. Whatever you have publicly available someone can copy. Photos, names, details. With this, they create an account duplicating yours. The play here is that they will then go through your friends list (if it is publicly available), add your friends and then have a message they would send to a friend. Something like “I am in trouble and need help, can you send me R100-200”. The “Play” here is that whoever they message will be concerned but not realize your message is suspicious. If you, yourself get a message like this then ask the person a question that only you 2 would know.
- “Where did Peter (her son) get married?”
- “Where did we first meet?”
- “What is my dogs name?”
If they can’t answer this you know the account is compromised. From here on out, report the profile and use an alternate communications method to notify them, the real them.
How do you combat this? Simple. Turn up your privacy settings, turn off publicly sharing your photos, your friends list and anything else unnecessary.
What to look out for in the future
If you have a complex and unique password, with 2FA you should be fine. But what should you keep an eye out for?
If someone such your friend, your cousin, your partner, your mother sends you a message with a link or sharing a post that you feel requires you to hurry up and open it…STOP! Below is an example.

Also, as mentioned above, if you get a message from someone you know, about needing to do something urgently, or send money, VERIFY it is them and if that does not work, call them and verify. What can also work is bombarding them with messages. Sometimes your account can get taken over, but the attacker won’t have changed your email or password, and therefore they still have access. If you bombard them with messages, they will see it, and when they respond, tell them to read this article and then change their passwords!
Lastly, if you see a friend post something that looks off, with a link, tell them!
Lessons learnt
The lessons are small and few, but rather important.
- Use unique and complex passwords, ideally with a password manager
- Enable 2FA
- Tell your friends about this stuff
- Dont click on stupid links
- Be more aware
What can I do to help?
- Share this with friends and “Influencers”
- Tell your friends
- Advocate complex passwords through password managers and 2FA.
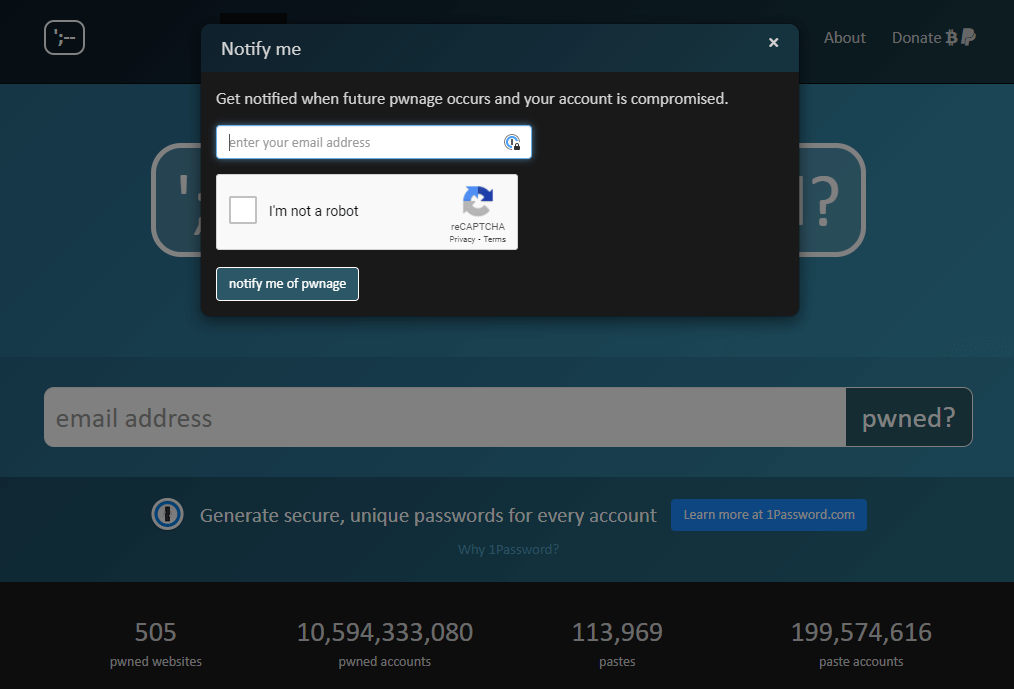
- On HaveIBeenPwned you can add your email address and you will be notified if any of your accounts get breached or leaked. And it is FREE!
Interesting Reading Material
Please go check out our recent technical blog on Password Cracking or the video on Youtube !
Check out our friend Bushido’s write up on Operational Security Tips
A great talk from DEF CON, the worlds biggest Hacker Conference attended by 50000+ Hackers from all over the world. This covers security tips on social media and what those random and harmless surveys and “What Game of Thrones character am I” type posts are really after DEF CON 26 SE VILLAGE - Hannah Silvers - My Stripper Name Is Bubbles Sunset
Great video of a 200k strong IG account suffering an account takeover from a verified account How She Hacked My Instagram Account
References and Links
-
Mywot - Source of the Password cracking graphic - Also a great article about password strength and cracking.**
