0xcon 2021
Taking place on Saturday, 13 November 2021 from 09:00 to 15:00 (SAST).
0xcon started in 2017 as a South African conference aimed at building the Gauteng and ZA infosec community. The conference welcomes both the new and experienced alike, and works hard to keep things open and free to everyone.
Due to the pandemic, this year’s conference will be streamed to YouTube with discussion on the Hack South Discord server.
How to participate
- Check out our LinkedIn event and RSVP. Share this with your friends and colleagues!
- On the day, the event will be streamed on YouTube
- Please join Hack South Discord server for discussion and questions during the event.
- We will host some polls on Discord to gauge how people feel about certain topics…
Event Program
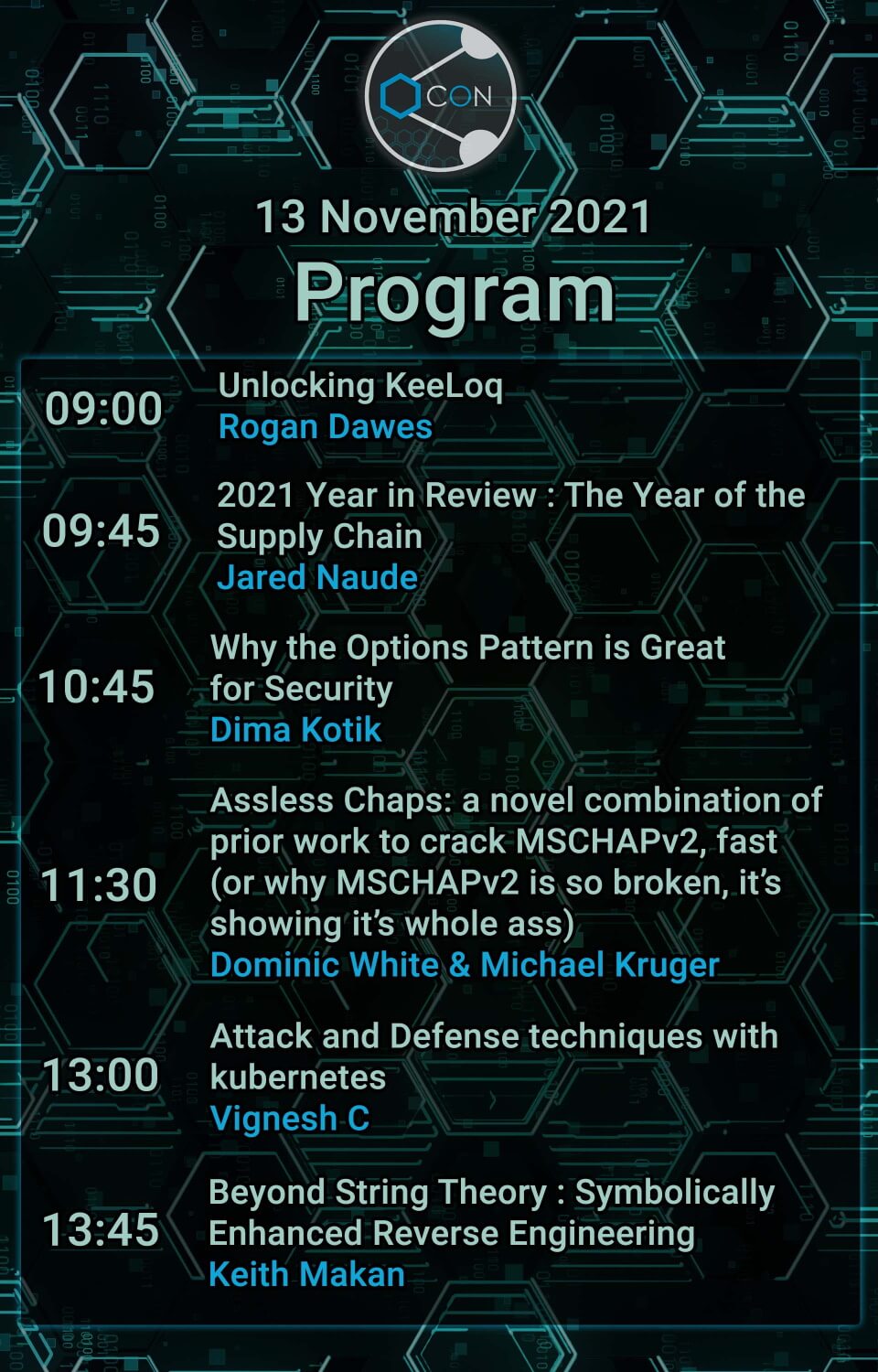
Unlocking KeeLoq - Rogan Dawes
KeeLoq Remote Keyless Entry systems make use of radio frequency transmissions to operate and have many known weaknesses. This presentation is a journey into bringing existing research together with manufacturer documentation to make implementing a complete Keeloq solution practical, ultimately repurposing a commercial receiver as part of a home automation system integration project.
I will demonstrate how I recovered the manufacturer key by extracting and reverse engineering the receiver’s firmware using a JTAG adapter and Ghidra. Next, I will cover decoding and decrypting the KeeLoq transmissions (verified using a logic analyzer), cloning the captured serial and sequence numbers to a new transmitter, and finally, how to export the received transmissions to a home automation system via an add-on WiFi-capable microcontroller.
About Rogan
Rogan Dawes is a senior researcher at SensePost and has been hacking since 1998, which, coincidentally, is also the time he settled on a final wardrobe. He used the time he saved on choosing outfits to live up to his colleague’s frequent joke that he has an offline copy of the Internet in his head. Rogan spent many years building web application assessment tools, and is credited as having built one of the first and most widely used intercepting proxies; WebScarab. In recent years, Rogan has turned his attentions towards hardware hacking; and these days many suspect him to be at least part cyborg. A good conversation starter is to ask him where he keeps his JTAG header
2021 Year in Review - The year of the Supply Chain - Jared Naude
Looking back at events that have taken place for lessons that can be learned is an important ingredient to enable forward insight, especially in the cyber security space. In this talk, I will go through the various security news, events and incidents of note that occurred in 2021 while adding some commentary and analysis from myself. This will primarily focus on the various supply chain attacks (SolarWinds, Codecov, Kaseya, etc) but will also cover trends in ransomware and malware, disinformation and Apple’s CSAM debacle.
About Jared
Jared is a Cloud Architect that specializes in enterprise cloud architecture and security; he is passionate about helping large organizations with architecting, building, securing and operationalizing cloud environments. Jared’s research interests and policy advocacy work involves cyber security issues that touch national security interests such as encryption, privacy, surveillance and disinformation.
Why the Options Pattern is Great for Security - Dima Kotik
Secure coding and functional programming are rarely mentioned in the same sentence. What if by applying a functional programming construct, we could write more secure code? Enter the Options Pattern, a hidden gem in securing your approach to object initialization.
The options pattern is a modern object initialization idiom. It involves writing a set of second-order functions returning options that roughly correspond to the initialization parameters. An option receives the object for initialization and applies a narrow modification to it.
The options pattern provides security benefits as side effects of encapsulation and separation of concerns. The main benefit is that it can make complex objects difficult to misuse, a necessary quality for modern cryptography, networking, and low-level libraries. It aids with code readability, reliability, and resilience. When properly implemented, the options pattern ensures sensible defaults, detects configuration conflicts at initialization, and provides logical grouping and consistency with entangled parameters.
In this talk, the speaker will explain how wider adoption of the options pattern improves code security for any project. Several examples will be examined and described as a demonstration of how to properly apply the secure coding options pattern in your own code.
About Dima
Dima Kotik is an application security engineer and lead curriculum contributor for Go, Python, and ES6 at @SecurityJourney. Aspiring to become a gentle FOSS maverick by age 60.
Assless Chaps: a novel combination of prior work to crack MSCHAPv2, fast (or why MSCHAPv2 is so broken, its showing its whole ass) - Dominic White & Michael Kruger
Cracking intercepted MSCHAPv2 challenge/response pairs from Wi-Fi or VPN attacks has long been known to be possible. However, unless the underlying cleartext password was common, this can take frustratingly long. Especially, for at-the-same-time attacks like the auto-crack-and-add we proposed in 2014 and presented at DEF CON. We’ll combine some prior work and release tooling to show how even extremely large hashlists can be run through in seconds.
MSCHAPv2 has several weaknesses, the first is that one doesn’t need the clear-text password, as merely having the MD4 hash (aka NT hash) of the password is good enough to prove to either a client or authenticator you know the password. This means we can use a technique proposed in 2020 by Sam Croley called hash shucking to use large NT hash lists such as the Have I Been Pwned set to determine the NT hash used in the exchange. We’ll go through the theory of MSCHAPv2, why the NT hash is useful and how to use it, as well as how Hashcat modes for cracking it were developed.
The second weakness relates to the work done by Moxie Marlinspike and David Hulton in 2012 where they found that because MSCHAPv2 breaks the NT hash into three parts, and pads the last two bytes with NULLs, it’s trivial to brute force this part (the ass). Then a brute force of the first two parts is performed using only a single DES round by iterating the entire DES keyspace with an FPGA. However, most of us still don’t have our own MSCHAPv2 cracking FPGA rigs, and this attack isn’t widely available or practical. Instead, if we limit our input hashlist to only those with the matching last two bytes, we can perform a far more efficient hash shucking attack against the exchange. We will go through the theory of MSCHAPv2 in use here and the optimisations devised with an associated tool.
Finally, we’ll end on why we think MSCHAPv2 needs to finally die the death it has deserved for so very long.
About Dominic and Michael
- @singe - Guy, Some @ Orange Cyberdefense’s SensePost team
- @cablethief - Random, Joe @ Orange Cyberdefense’s SensePost team
Attack and Defense techniques with kubernetes - Vignesh C
In modern day environment blue team had to face lot of issues with container security, This talk aims to address the overall summary of Kubernetes security and common mitre matrix scenarios, It also explains how to implement end to end fully hardened environment which will help to securely monitor the cloud and containers.
About Vignesh
Vigneshc has a few security hall-of-fames and CTF wins. He has worked on a wide range of topics in security, including Red Teaming, Infrastructure Pentest, Purple Teaming, Forensics & Incidence Response, Cyber Threat Intelligence, Cyber Footprint Assessment, and Application Pentesting. Pentester and just another guy whom plays around with 0’s and 1’s.
Beyond String Theory: Symbolically Enhanced Reverse Engineering - Keith Makan
Reverse engineering software from binary executable forms remains a key challenge for modern software analysis. Common techniques include running good old strings or grep and hoping for the best before trying to derive control flow graphs, call stacks and resolve cross references via complex disassembly frameworks. Beyond cursory string inspection, symbolic execution gives us the power to emulate execution, derive concrete test cases and prove reachability to interesting points in a static binary, and with Angr we can leverage that power in Python. In this talk the speaker will unpack basic concepts introducing symbolic execution in the Angr Framework and show methods to apply this to discovering content secrets, log data, etc.) in ways strings or static inspection would be incapable of. The talk walks through examples from real world binaries including common utilities as well as CTF challenge binaries
About Keith
Keith Makan is a security consultant with 6+ years of experience in delivering secure assessment of code and applications in various industries spanning companies across the globe. Keith has consulted at large businesses in software/internet based technologies and remains eager to learn new ways to assess and scrutinize modern applications. Keith’s expertise include Secure Code Review in various languages, Android and Web Application assessment, Network and Infrastructure assessment as well as a growing expertise in Reverse Engineering, Binary Analysis and Social Engineering.
During the span of his career he has published two books in the information security field namely, “The Android Security Cookbook” and “Penetration Testing with the Bash Shell”, and is currently pursuing his masters in Computer Science with a focus on Binary Symbolic Execution.
Conclusion
We look forward to seeing everyone at our event!
