0xcon 2023
0xcon is aimed at bringing together the local cyber security community to share knowledge and to network with like minded individuals. This event is very much by the community for the community, so whether you’re a seasoned expert or just starting out, we would love to welcome you to our conference as we enhance our understanding of the cyber security landscape. The conference covers a wide array of topics including cyber security best practices, threat intelligence, IOT security, ransomware, incident response, cloud security, data privacy, application security, penetration testing, coordinated inauthentic behavior and disinformation.
0xcon returns for another year of sharing information in the community. More information about the conference is set out below.
How to participate
- 0xcon 2023 will take place on Saturday 4 November 2023 from 09:00 to 17:00 at the MTN Innovation Center (214 14th Avenue, Fairland, Johannesburg).
- Tickets are R200 and can be purchased from Quicket.
Event Program
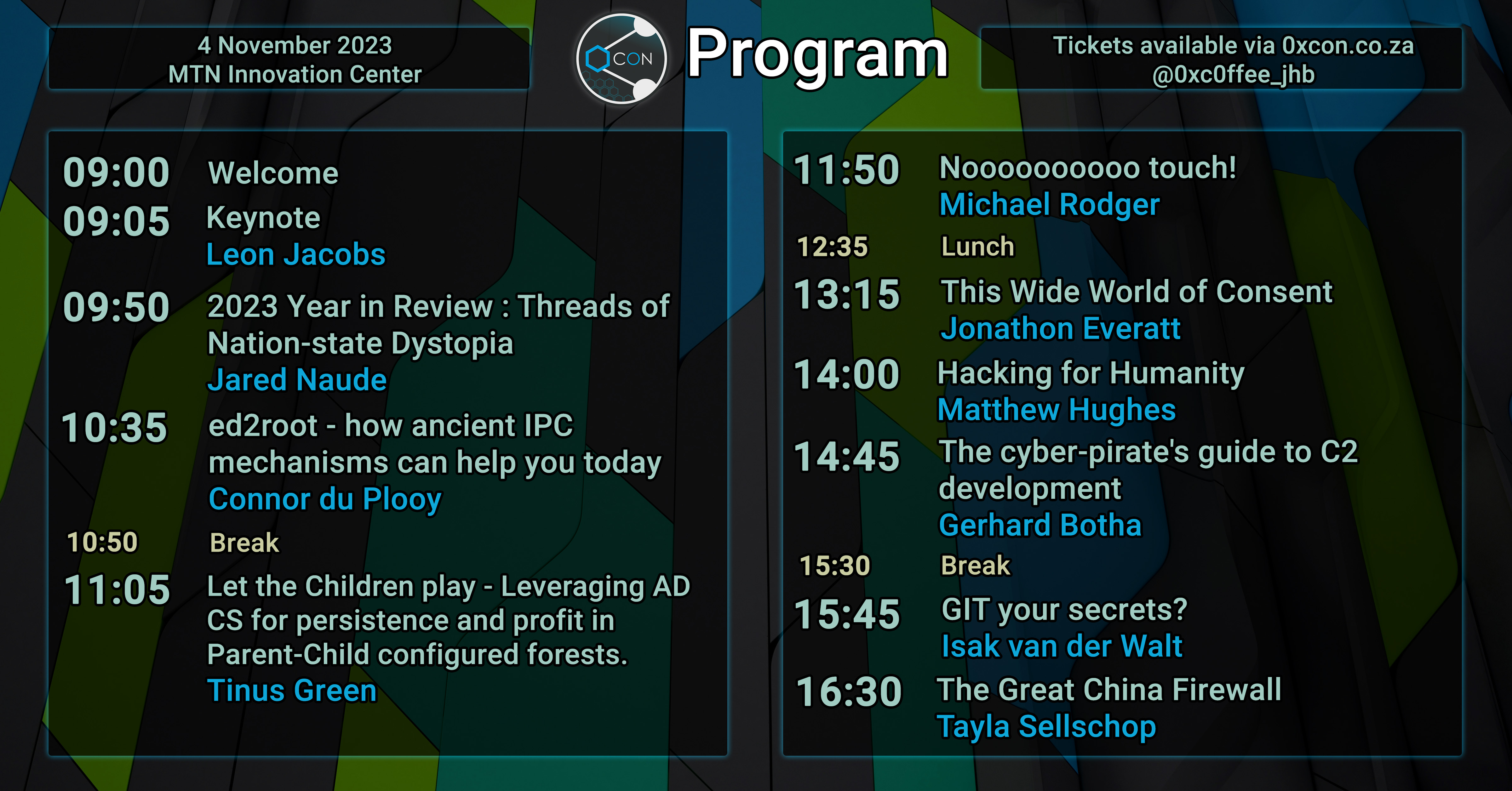
Keynote - Leon Jacobs
Some thoughts on the benefits of research.
About Leon
Guy who likes to eat with two forks. Hacker @sensepost
2023 Year in Review: Threads of nation-state dystopia - Jared Naude
Retrospectives are a great tool to look back at past events to understand what went right and what went wrong. In doing so, we can identify lessons that can be learned and what needs to be improved. This talk will be focused on analyzing the major cyber security events of the past year along with insight, analysis, and commentary on what it means for the wider cybersecurity community. 2023 saw a massive shift in the strategy and playbooks of state sponsored actors in targeting, tactics, and methods.
In this talk, we will discuss the impact and significance in the shift of nation-state activity while looking at events of the past year, even if they are not nation state related. Some of the topics and events that will be covered in this talk include the following: How Ukraine has countered Russia’s cyber and disinformation, how Russia is struggling with Chinese technology, the US’s overreaction to TikTok, Chinese state-sponsored activity into US critical infrastructure and US department emails, the rise of commercial spyware and its implications, why the Cyber-Safety Review Board (CSRB) is doomed to fail, the impact of adversarial AI and LLMs, cross tenant cloud vulnerabilities, troubling privacy legislation; and the impact of lost key material.
About Jared
Jared is the Head of Security at Synthesis, where he specializes in enterprise cloud architecture. Jared is passionate and deeply committed to guiding large organizations through the complexities of architecting, securing and operationalizing enterprise cloud environments. Beyond Jared’s professional responsibilities, Jared is an enthusiastic advocate for community building, serving as the organizer of several local security events, including 0xcon, BSides Cape Town, and BSides Joburg. Jared’s research focuses on cybersecurity topics that intersect with national security and foreign policy issues such as encryption, privacy, surveillance, disinformation, and nation-state activity.
ed2root - how ancient IPC mechanisms can help you today - Connor du Plooy
This talk will go over how I found a vulnerability in a text editor on MacOS. Other variants of this vulnerability have been identified in other packages as well, and even though the APIs used by these packages have been deprecated for a really long time, it is still around in some software.
The vulnerable component is exposed over IPC, so the talk will be broken down in to the following sections:
- An introduction to the vulnerable component (+- 5 minutes)
- A brief demonstration of the vulnerability (+- 2 minutes) (how to get root from a text editor)
- A primer to show how the software can be identified by combining static/dynamic analysis techniques (+- 2 minutes)
- QAs
Key Takeaways:
- Why using deprecated APIs is always a bad idea
- How to identify vulnerable software
- Understand the abstractions you build on
About Connor
I work as a mobile security consultant for MWR CyberSec. I love security but specifically have a passion for mobile applications and reverse engineering.
Let the Children play - Leveraging AD CS for persistence and profit in Parent-Child configured forests - Tinus Green
In 2021, Active Directory Certificate Services (AD CS) came under scrutiny because of the opportunities it provides attackers for credential theft, domain and forest privilege escalation, and persistence. Since then, it has become a household name for red and blue teams alike. Unintended consequences and additional attack avenues are continually being discovered. This talk will cover new discoveries in this space from two perspectives:
- Lateral Movement - Noisy compromises of the Parent domain through Golden or Diamond tickets to get to other Child domains are a thing of the past
- Cross-Domain Escalation - A newly discovered default permission misconfiguration allowing forest-wide persistence from any Child domain
This talk will not only demonstrate these newly discovered attacks and the tooling released to exploit them, but also provide insights into mitigation methods that can be applied to close these attack avenues and the detection methods that can be used to discover them.
About Tinus
Tinus is currently the Head of Consultancy, where he leads the entire consultancy division, including all service areas and the research division. Previously he was the Service Lead for the Network Security and Application Security divisions and second-in-command for these services globally. In these services, he helped innovate in the respective service space to ensure that MWR provides top-tier, research-driven services to their clients.
In the Cyber-defence field, he assists executives and senior management teams of several strategic clients in an advisory capacity in helping solve business and operational security challenges. This includes creating long-term roadmaps for cyber resilience and using the tools available to the organisation to better track and understand their security posture.
He was responsible for creating a Technical Tabletop Exercise solution. This service simulates real-life attacks in a mock environment to provide training opportunities for Computer Security Incident Response Teams (CSIRTs) to enable companies to improve their Incident Response and Management processes.
Since Tinus has a passion for training, he is also involved as a content engineer for TryHackMe to create cyber security training content and a part-time final-year project leader at the University of Pretoria for their EEC Engineering division.
Noooooooooo touch! - Michael Rodger
A few years ago, a new addition to the standard lineup of access control equipment quietly appeared - the humble “No touch” sensor. These mostly replaced physical buttons, the typical use case being letting yourself out from the “inside”, where the “outside” would have some form of control such as a keypad, RFID scanner, biometrics, etc. Naturally if you were already inside, you wouldn’t have to authenticate yourself to leave. Fast forward to 2020 and “things you didn’t have to touch” were all the rage, so these started popping up all over the place (according to my observations). I was curious as to how they worked, and whether the range could somehow be manipulated. I had a hunch that they functioned by reflecting infrared light of some sort and I confirmed this by buying one and taking it apart. I came up with an idea to brute-force these to open with an external light source, and then high-powered infrared LED behind a lens to extend the range significantly. This was attractive because they are frequently placed on “inside” of glass doors where the “outside” requires authentication, so having a high-powered “no touch blaster” would let you into places you shouldn’t be :) My initial research revealed that they seem to be more secure than I’d hoped, so I’m now less confident that beating them is even possible, but I have a few more ideas around what could be tried. At a minimum, this will be a talk about taking a piece of hardware and dissecting it to figure out how it works, and essentially security testing it. General hardware security methodology and my journey from wondering, to opening, to what I learned about the devices. Best case scenario, I find a method that works and talk about the weaknesses and end up with a gadget in my red-team bag of tricks.
Also, the title is “noooooooo touch” with 10x o because the extended range, so I’m really not touching it.
About Michael
Starting out as an electronic engineer, I quickly learned that my penchant for disassembling things and figuring out how they functioned also meant that I liked breaking things. I joined the dots to infosec and since around 2013 I’ve been involved in the ZA hacker community. I’ve been helping with conference and meetup organising and badge building for most of the time since then, and in 2023 I made things official by joining the research team at Orange Cyberdefense. I still tinker with hardware every chance I get, either fixing or improving something I have, or building something new. I’ve already come to terms with the consequences I’ll one day face when I teach my 2 small kids to question and dismantle everything, although my wife has already put a moratorium on bringing home broken electronics because “I’m sure I can fix this”. I don’t like long walks on the beach because the sand gets everywhere and it smells like fish. I do like mountain biking though. Sorry, did you say “brief?”
This Wide World of Consent - Jonathon Everatt
With the advent of cloud based technologies and identity management solutions; as well as the widespread adoption of these technologies by businesses and users has introduced new attack vectors that malicious actors can try abuse. One of these is a new type of phishing, called consent phishing.
In Consent Phishing, an attacker-controlled application requests dangerous or sensitive permissions over a user’s account or organisation’s tenant. The goal of Consent Phishing is to gain the necessary authorisation (consent) over an aspect or portion of a user’s account. The consent grants are managed through an Identity Provider using the OAuth 2.0 framework; examples of these technologies would include Azure, Facebook, and Discord.
This talk will explore the concept of consent phishing and utilise examples of consent phishing in Azure to illustrate the explanation. The talk will focus on both the offensive perspective and the defensive perspective of the attack and its relevant indicators of compromise. The talk will also show a high-level investigation of how other technologies tackle the problem of consent phishing.
About Jonathon
Hi, my name is Jonathon Everatt, I am a CyberSecurity Consultant at MWR CyberSec and the lead of the Web Application Security Service. I graduated from UCT in 2021 with a First Class Computer Science Honours degree. I learnt CyberSecurity through the TryHackMe platform and others where I go by the alias “Fluffiest Bunny”.
Hacking for Humanity - Matthew Hughes
Have you ever tried your hand at GeoGuessr, the online game that challenges you to guess your location from random street views? In my talk, I’ll unveil the surprising connections between the problem-solving skills used in this game and the world of hacking and cybersecurity.
My journey started with GeoGuessr, where I noticed how similar the way we think during the game is to the thought processes of hackers and cybersecurity experts. It was like learning to hack the real world without realising it!
During the talk, we’ll delve into the fascinating world of seemingly ordinary photos and videos on the internet. I’ll emphasise why it’s crucial for all of us to be cautious about what we share online. You’ll also hear real-life examples of how geolocation, the art of figuring out locations based on clues, has been used to find terrorist compounds and provide crucial evidence in missing persons cases.
But it’s not all about risks. I’ll also demonstrate how we can harness geolocation skills for positive purposes. Through this research I was able to develop an AI tool using machine learning that can analyse and identify street bollards, a key factor in geolocation.
Join me for this talk, where we’ll explore the intriguing connections between a simple online game and the dynamic world of geolocation in cybersecurity.
About Matthew
My name is Matthew Hughes - I’ve been a Security Analyst at Orange Cyberdefense’s Sensepost team for over a year now. Based in Cape Town, I’m a high school dropout that has always been fascinated with how technology works, but more importantly how it could be tampered with.
The cyber-pirate’s guide to C2 development - Gerhard Botha
Covering the basics and considerations into creating a Command & Control framework. Going over the basics of a C2 and discussing the why’s and where’s of their usage. Then diving into the different elements to take into account when making design choices. We’ll also be covering how to start your own journey. Finally, what you need to look out for when the project is ready to go onto the next step.
About Gerhard
A human with a passion for malware development, offensive security research and tooling. Likes hacking and gaming, also likes game hacking, does not like scope-creep. During the day, this human pentests and annoys co-workers with memes. His boss probably thinks he doesn’t do much work.
GIT your secrets? - Isak van der Walt
This will be the same talk as I presented at 0xcoffee, with some minor updates if time permits. The talk covers three primary aspects:
- A technical overview of how the git version control tool works.
- Some inherent and typical security issues related to git.
- Prevention and resolution of the prior demonstrated issue.
This talk does not contain any “new” research but rather just a full presentation of the git internals, the known inherent vulnerabilities and their resolution - all of which have been previously documented.
The first section aims to provide an overview for people not familiar with git, before diving into the building block - so called “plumbing” - tools utilized by git to perform its version control. This serves to provide a better understanding for the vulnerabilities as well as how to better utilize git.
The second section covers inherent vulnerabilities such as lack of author validation and secrets in version control histories, some of which will be accompanied with a basic demonstration. This also provides a baseline for what to look for from a defender’s perspective
Finally the preventative measures and resolutions will be covered to address the aforementioned issues. Some simple measures in addition to the knowledge of the vulnerabilities can vastly reduce most of the surface area and risk associated with the covered vulnerabilities.
About Isak
Isak is a Junior security analyst, fresh out of university this year. Previously did some web and embedded development and later sysadmin work part time before and during my studies. Also serving as a staff member at Hack South and as an organiser for BSides Cape Town.
The Great China Firewall - Tayla Sellschop
The talk details living in China. It covers grappling with censorship and the distinction between state-sponsored and independent VPNs. It goes over how the firewalls in China work and the various hardware limitations that consumers face. My life in China, how internet access varies depending on when government committees and conferences that take place. How information and lack thereof during the beginning of the COVID outbreak Navigating wechat censorship and the hardware challenges of IOS and Android Why sometimes you need to go to Hongkong or Taiwan if you want the right app store China vs the rest of the world app stores
About Tayla
Hi!! I’m Tayla !! I’m a junior cyber security analyst at Telspace. I have a passion for cyber forensics and crytography. I got into the industry because I wanted to make everyday people safer. I have a backgroung in law and I lived in China for several years.
Conclusion
We look forward to seeing everyone at our event!
